Top 10 Best android spy apps.
t's worth to note that there are plenty of Android spy apps available on the Google Play Store, but mentioning all of them is not possible. So, in this article, we have listed the one that's popular and used by many. So, let's explore the list of best spy apps 2019.

This app permits users to capture images secretly. This app provides a smart way to shoot photos with a hidden camera interface so people wouldn't notice that you are taking pictures of them. Also, every sound and flash etc get disabled in this app.

This is an awesome app to record even low voices. By this app, you can place your phone in the other room and can listen to the voices of that room by your Bluetooth handset. This app actually records the sound and then amplifies its recording and give you the amplified clear voices.
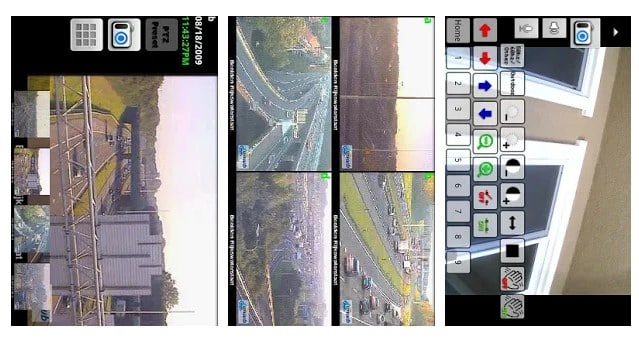
This awesome app allows to remotely view and control your IP Camera, DVR, Network Video Recorder, traffic cameras, CCTV or WebCam from an android device. In its new version, you can also get the notification on detecting motion on the device. This app can automatically start recording whenever it detects motion.
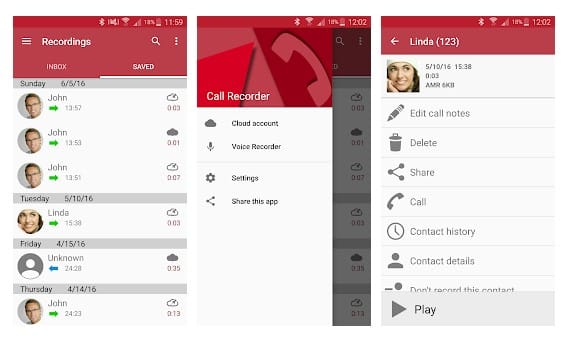
This is another best Spy App that one can have on their Android smartphone. This app gets automatically launched whenever you make or receive any call. It records all the conversation b/w speakers and also the surrounding noise of the device in which it is installed.

This is another good spy app to remotely monitor SMS, Photo, Location, call logs and many more things on an Android device. This will exact location of the targeted device through a web-portal even if GPS disabled on the target device. The app comes with the three-day free trial option.
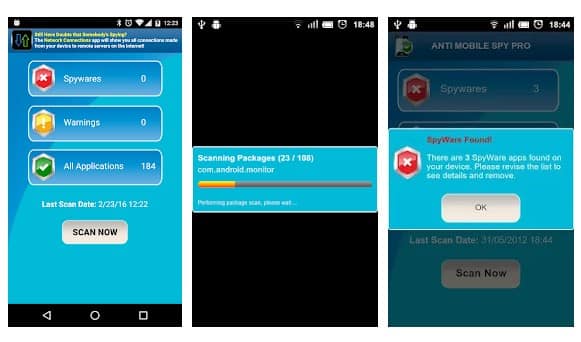
You don't know whether you had installed any spyware software on your phone? Use this app to instantly find the spyware. The Android app uses advanced detection techniques to detect new spyware. So, with this app, you can easily protect yourself from Android spyware.
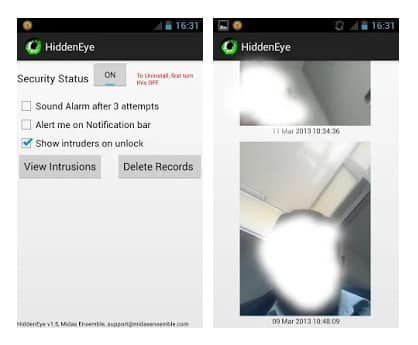
Ever wanted to know who tried snooping on your phone while you were away. Your friends or family member might have tried to unlock your phone. Hidden Eye is a simple app with no frills that will photograph the person when they try to unlock your phone.

Applock is the most downloaded app lock in Play Store. Protect privacy with password, pattern, fingerprint lock. AppLock can lock Facebook, Whatsapp, Gallery, Messenger, SMS, Contacts, Gmail, Settings, incoming calls and any app you choose. Prevent unauthorized access and guard privacy. Ensure security.

With this app, all outgoing, incoming and missed calls coming from private contacts will be deleted automatically from calls Log of your phone! No icon of this app will appear in your list of applications on your phone.
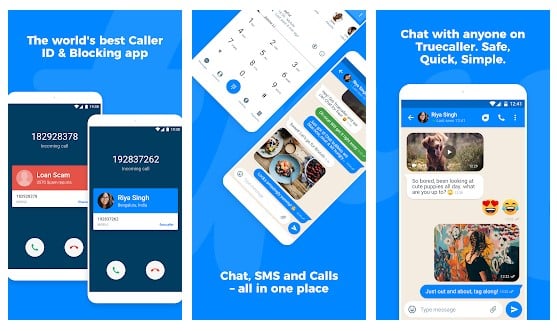
Truecaller is the only dialer you'll ever need with the ability to identify unknown callers and block unwanted calls. See names and photos of people who call, even if they aren't saved in your phonebook. And know when friends are free to talk, making your calling experience smarter and more delightful.

You can use the cell tracker Android app to keep track of the location of your smartphone. With the help of this app, you can track all the locations you have visited in the last few days with your Android phone. To check the locations visited you have to launch the app and click on "View Now". No need to turn on the GPS.

With the help of this app, all outgoing, Incoming and Missed Calls coming from private contacts will be deleted automatically from Calls Log of your phone! No icon of this app will appear in your list of applications on your phone.

This is another Spy app on the list which provides one-touch to capture image feature. The app actually has lots of useful features. With the help of this app, you can find your lost phone because this app allows you to set up a number. When you lost your phone, just SMS to this phone and it will take a picture and upload to drive.

Truecaller is a popular Android app which is used every day to identify unknown calls, block spam calls and spam SMS. It filters out the unwanted and lets you connect with people who matter.

Whoscall, the best caller ID App that identifies unknown calls and blocks annoying spams, robocall & telemarketing with more than 50 million downloads and over 1 billion numbers data. It also got the call blocker that can be used to blacklist or whitelist contacts stored on your smartphone.
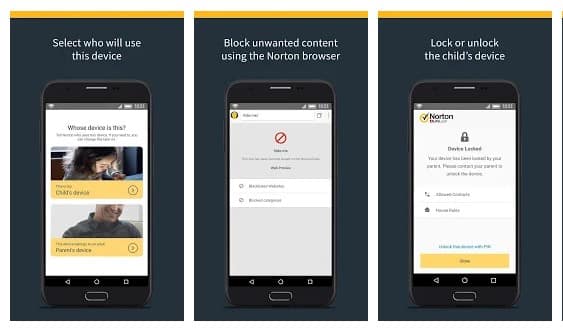
Norton Family parental control is basically an Android app that is meant to keep kids safe online. However, this is nothing sort of a spy app. The app can help you to supervise online activity. You can easily keep track of sites which your friend visit and what they search if you install Norton Family Parental control on their phone.

The app doesn't help users to spy on others. But, it can give you a detective type feeling. Smart hide calculator is a fully functional calculator app but with a little twist. Once you enter the password and press the '=' button then boom you are presented to an interface where you can hide, unhide pictures, videos, documents or files with any file extension.

Ever wanted to know who tried snooping into your phone while you were away. Your friends or family member might have tried to unlock your phone. Hidden Eye is a simple app with no frills that will photograph the person when they try to unlock your phone.
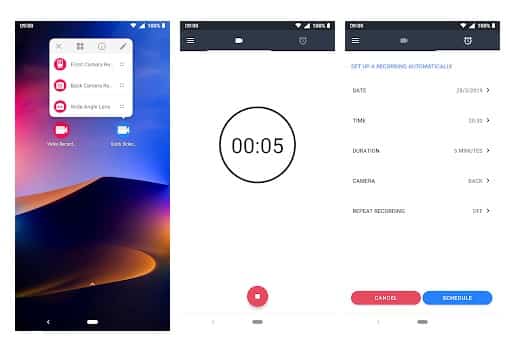
This is another best Android spy app that helps users to record what's happening behind them. Background Video Recorder is basically a camera app that records videos silently on the background. The app eliminates the camera shutter sounds, camera previews and it can also record videos when the screen is off.

Kids Place is another best parental control app in the list and its meant to protect your kids' online activities. However, if you don't have kids, you can use the app to track other devices. The app gives you full control over other devices and you can control everything including calls, text, internet browsing, apps, etc.
@EVERYTHING NT
Related news
- Fake Hacking
- Programa Hacker
- Hacking Etico Que Es
- Hacking Tools
- Hacking News
 "Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...
"Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...



















































